| Welcome to The Cybersecurity 202! The Supreme Court doesn't lend itself to great film treatments, but "First Monday in October," starring Walter Matthau and Jill Clayburgh, is pretty good. Below: A ransomware gang hacked France′s Justice Ministry, and Hungarian civil rights advocates are challenging the country′s use of Pegasus spyware. | The next Supreme Court justice will face mounting cybersecurity cases |  Supreme Court Justice Stephen G. Breyer announced plans to retire. (Kevin Lamarque/Reuters) | | | Supreme Court Justice Stephen G. Breyer, who announced plans to retire this week, dealt with only a handful of major cybersecurity and privacy cases during his 28 years on the high court. But the experience of his successor is likely to be far different. The next decade is set to be a seminal one for cyber and privacy at the high court as cases involving dramatic shifts in technology, how it's incorporated into daily life and what happens when it's vulnerable to hacking finally work their way to the Supreme Court for review. Breyer's successor, who President Biden has said will be a Black woman who he plans to appoint by the end of next month, could play a leading role in sorting those questions out. Here are three big issues the court could address: 1. When do companies have to pay out for data breaches? | | Historically, consumers have had a tough time suing companies with inadequate cybersecurity protections which are then hacked. Courts are split: Federal courts agree that customers must have suffered some actual harm to have standing to sue companies after a breach. But some federal appeals courts say it's harm enough that customers' data was stolen. Others say customers must have suffered some more tangible harm like having their identity stolen and losing money. That barrier is particularly difficult to overcome because most people have been the victims of multiple data breaches. So, when their personal information is used to run up credit card bills or for other nefarious purposes, it's very difficult to prove that happened because of a specific breach. "Showing that link is difficult and not as straightforward as some might think because it's difficult to trace where data comes from," Jeffrey Vagle, a Georgia State University law professor who focuses on cybersecurity, told me. It's highly likely the Supreme Court will take a case in the next decade or so that tries to clarify the question, he said. 2. Can companies block cybersecurity researchers from finding bugs in their products? The Supreme Court made its biggest move into cybersecurity to date last year when it reined in the nation's main anti-hacking law, the 1986 Computer Fraud and Abuse Act (CFAA), in the case Van Buren vs. United States. That ruling settled some basic questions about what counts as hacking and what doesn't, but it also left a lot of unanswered questions that future cases will have to settle. The justices basically ruled that it's not hacking if you only access parts of a computer system that you already have permission to access. | | The plaintiff in the case was a police officer who accepted a bribe to gather information from a police database. That may have been illegal for other reasons, but the justices feared that calling it hacking under the statute would open the door to criminalizing common activities such as checking social media or online shopping on a work computer. But the ruling left hazy what happens when people break rules that are overly restrictive such as violating a website's onerous terms of service. That's often the case for cybersecurity researchers who are threatened with CFAA lawsuits when they violate websites' terms of service to search for dangerous computer bugs. 3. What's a reasonable search and seizure in the smartphone age? If there's one area where the Supreme Court has grappled with the effects of technology more than any other, it's the Fourth Amendment right against unreasonable search and seizure. The court has stepped in a handful of times to rein in tech-enabled methods that law enforcement has used to collect troves of data without a warrant. | - The court ruled in United States vs. Jones in 2012 that Washington, D.C. police exceeded their authority when they attached a digital tracker to the bottom of a suspect's car and tracked him for a month to collect evidence of criminal activity without a valid warrant.
- The court ruled in Carpenter vs. the United States in 2018 that the FBI exceeded its authorities when it collected information without a warrant about the approximate location of a suspect's cellphone to prove that he was near the location of multiple robberies.
| | There are bound to be numerous similar cases that reach the court in the coming years as the ways police can collect data expand. "The courts are going to have to conduct new assessments based on new invasions of privacy that new technology makes possible," Jeff Kosseff, an assistant professor of cybersecurity law at the U.S. Naval Academy, told me. On a related note: The court will also likely grapple with when and how people suspected of a crime can be forced to unlock their phones and other devices using passwords or biometric signatures. Various courts have reached different conclusions about whether that violates the Fifth Amendment right against self-incrimination, but the Supreme Court has yet to weigh in, Kosseff said. | | None of the judges being floated as likely successors to Breyer has a lengthy track record in cyber and privacy cases. But they're all in their 40s or 50s, which may suggest a closer familiarity with technology and its pitfalls than some older justices. That also means they're likely to have a lengthy tenure on the court during which they'll face cybersecurity questions that are as difficult to imagine now as the security issues spawned by smartphones might have been when Breyer joined the court in 1994. "Something like the smartphone, people were thinking about it, but it was like science fiction," Vagle told me. "Ten years from now, who knows what technology we'll be using then, let alone throughout the tenure of a Supreme Court justice." | | |  | The keys | | A ransomware gang says it hacked France's Justice Ministry |  It's not clear what data was stolen from the ministry, which is led by Justice Minister Éric Dupond-Moretti. (Valentine Chapuis/AFP/Getty Images) | | | The hackers are threatening to publish "all available data" in two weeks, Security Week's Eduard Kovacs reports. The hackers claimed responsibility for the breach just one day after an independent French auditor said the ministry had made progress on cybersecurity but still had significant work to do. The Justice Ministry told Security Week that it is aware of the group's claim and has launched an investigation. The ransomware group, known as LockBit, is also connected with hacks targeting major corporations like Danish wind turbine firm Vestas and the consulting firm Accenture. The gang is known for threatening to publish data if its ransom demands aren't met, Kovacs reports. | Iranian officials are investigating a rare hack of state television | | It's an extraordinary breach because Iranian state television is believed to be operated by the country's cyber-savvy intelligence services, the Associated Press's Jon Gambrell reports. The hacked broadcast depicted leaders from the exiled opposition group Mujahedeen-e-Khalq (MEK). A state broadcaster said MEK was behind the "extremely elaborate" hack, Bloomberg News's Golnar Motevalli and Patrick Sykes reported. MEK spokesperson Shahin Gobadi didn't claim direct responsibility for the breach and said it appeared to have been done by "supporters of the MEK and resistance units within the regime's radio and television stations." The MEK has come under scrutiny for its cyber and other operations. Facebook has removed troll farms related to the group, which is largely based in Albania. The Intercept reported that a well-known Twitter critic of Iran is actually a made-up persona created by the MEK. The Obama administration removed the group from a government list of terrorist organizations in 2012. | Hungarian civil rights advocates and journalists are launching legal challenges to the country's use of Pegasus spyware |  Hungarian Prime Minister Viktor Orban has come under fire for what critics say is an autocratic turn. (Akos Stiller/Bloomberg News) | | | The Hungarian Civil Liberties Union (HCLU) plans to file complaints with data regulators and authorities who oversee the country's security services, Claire Parker reports. If those go nowhere, the group — which represents four clients targeted by NSO Group's Pegasus spyware — will resort to legal action. In Hungary, victims of Pegasus have included two journalists and a businessman who didn't want to be identified. Critics have compared the use of Pegasus in Hungary to the country's communist past. The country's right-wing prime minister, Viktor Orban, has been accused of moving toward autocracy and undermining Hungary's democracy. The country's use of Pegasus has drawn particular attention because Hungary is a member of the European Union. "The organization will also bring 'a multitude of lawsuits' before the European Court of Human Rights on behalf of a wide swath of civil society actors and journalists whom the HCLU say are exposed to surveillance," Claire writes. The HCLU is also filing a complaint with the European Commission on behalf of Belgian-Canadian student activist Adrien Beauduin, who was studying in Hungary when he was targeted by Pegasus, which the group says violates European Union law. NSO does not disclose the identities of its customers, but a former NSO employee speaking on the condition of anonymity told The Post last year that Hungary's government was a client. The country says it abides by the law when using surveillance technologies. An investigation by The Washington Post and 16 media partners last year found that Pegasus was used to target human rights advocates, journalists and executives in Hungary, India, Mexico and other countries. | | |  | Chat room | | | The State Department was hit with massive email problems yesterday, but signs so far point to a technical glitch rather than anything malicious, my colleague John Hudson reports: | 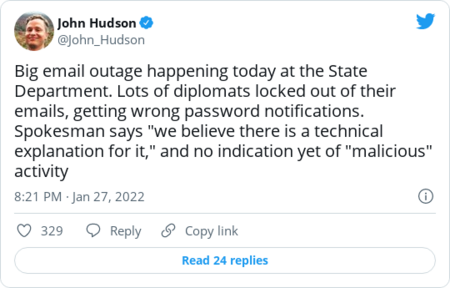 | | | | | |  | Global cyberspace | | | |  | National security watch | | | |  | Government scan | | | |  | Privacy patch | | | |  | Industry report | | | |  | Securing the ballot | | | |  | Cyber insecurity | | | |  | Daybook | | - FBI Director Christopher A. Wray speaks at the Reagan Library on Monday.
- The Brookings Institution hosts an event on ethical use of artificial intelligence on Monday at 11 a.m.
- BSidesTLV founder Keren Elazari discusses hacker cultures at a Strauss Center event on Thursday at 1:15 p.m.
| | |  | Secure log off | | | Thanks for reading. See you Monday. | | |








No comments:
Post a Comment