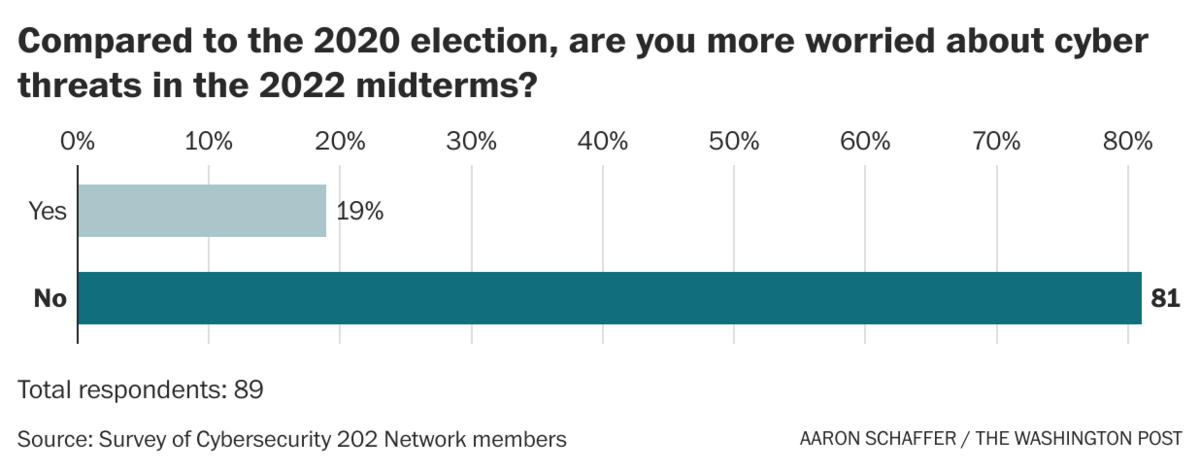
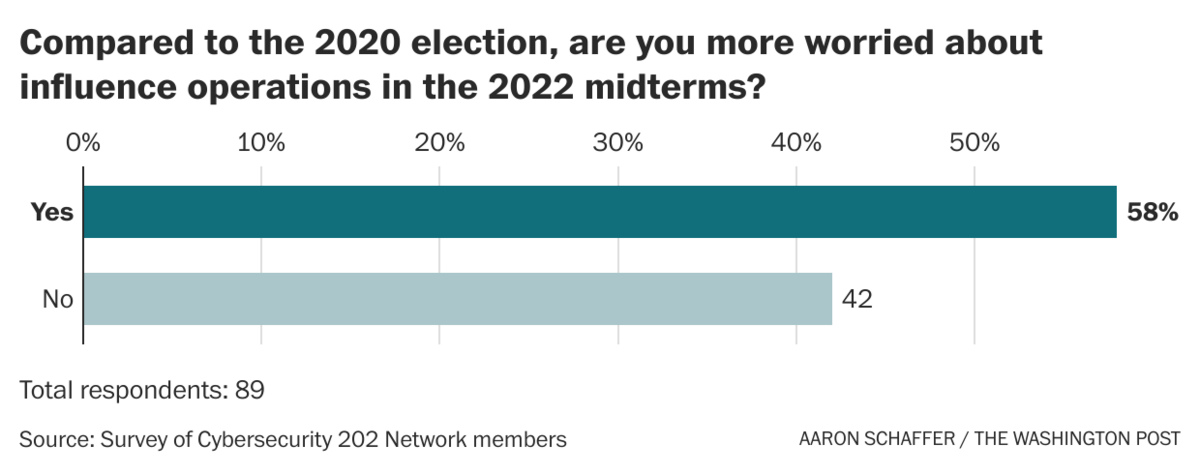
| Welcome to The Cybersecurity 202! Happy Halloween, too. I spent a goodly portion of the weekend watching horror movies and shows. "Barbarian" tops the list among new movies, is the short answer, but Guillermo Del Toro's horror anthology on Netflix was pretty swell, too. Below: U.K. politicians are calling for an investigation after a report that Russia hacked former prime minister Liz Truss's phone, and the U.S. government convenes a group of allies for a summit to talk ransomware. First: | Our Cyber Network: Influence operations are more worrisome this year than in 2020 |  There is just eight days until the midterm elections. (Scott Olson/Getty Images) | | | There are two main ways bad actors can try to influence U.S. elections: by manipulating voters or by breaching election equipment or software. Our group of cyber experts say they're more worried about the first possibility but less worried about the second in this upcoming election compared to 2020. The midterm elections are next week (yes, really) so we polled our Network experts group about how they're feeling. A majority, 58 percent, said they're more worried about operations designed to manipulate voters in the midterms compared to 2020. But just 19 percent said they're more worried about cyberthreats this time. | | Over the weekend, Cybersecurity and Infrastructure Security Agency Director Jen Easterly repeated her mantra about the midterms on CBS's "Face the Nation" on Sunday, arguing that the midterms offer a "very complex threat environment" where "you have cyberthreats, you have insider threats, you have rampant disinformation." | - CISA nonetheless has "no information about specific or credible threats to disrupt or compromise election infrastructure," she said.
| Influence ops versus cyberthreats | | More experts are worried about influence ops than cyberthreats. Most were either more concerned about influence operations but not cyberthreats or not more concerned about either type of threat. "There was no real cyberthreat to the elections in 2020 that would have affected the outcome, but plenty of disinformation around the legitimacy of the election," said Katie Moussouris, founder of Luta Security. "Seditious disinformation was spread on social media via superspreader accounts that were suspended too late. Bots, traitors, and foreign influencers amplified the messages that the election was stolen, which led to a deadly insurrection that threatened the peaceful transfer of power." Said Debora Plunkett, a senior fellow at the Harvard University Belfer Center's Cyber Project: "While the need for vigilance in preparing for cyberthreats remains high during this election cycle, the bigger issue is the hostile political environment, the continued influence of election deniers and the overall state of our democracy. These elements create a ripe environment for influence operators, whether nation states or domestic actors, to create discourse and doubt in our democratic processes." Both those messages pointed to two frequent undercurrents: | - Concern about domestic disinformation campaigns, specifically from 2020 election deniers.
- Worry about the ability of those campaigns to flourish in the current political environment.
| | In some cases, experts saw an overlap between foreign influence campaigns and domestic ones. "We are in a hybrid war with Russia and they've co-opted many more useful idiots to undermine the integrity of the 2022 election than in 2020," said Chris Finan, president and chief operating officer of ActZero. A handful of experts pointed to Republicans explicitly. | | Foreign adversaries "are interested in a U.S. foreign policy that is more chaotic and incoherent, which is more likely with a Republican-controlled Congress," said Herb Lin, a cyber expert at Stanford University. "Influence operations require less technical skill than cyber operations and hence are easier to conduct; hence my greater concern about influence operations." | Not more worried about both | | The midterms are simply of lesser importance to foreign adversaries than years marked by a presidential race, said a number of experts who were not more worried about both threats in 2022. "I remain worried about cyberthreats and influence operations in every election," said Betsy Cooper, director of the Aspen Institute's Tech Policy Hub. "This being said, foreign nation states are more interested in presidential elections than midterms, so I would expect them to have dedicated more resources in 2020 than they will in 2022." Several respondents explained that they were equally worried about one threat or the other, compared to 2020 — thus, not technically "more" worried. Just as some experts gave federal and election officials credit for better protecting election infrastructure, Dave Aitel, a partner at Cordyceps Systems, said "it's worth giving the social media company some credit for establishing internal monitoring of influence operations and acting to shut them down." | | There's little reason to think the United States is sufficiently more prepared now than in 2020, said some who were more concerned about both cyberthreats and influence operations in the midterms. "Influence operations and election hacking are as old as elections," said Tor Ekeland, managing partner for Tor Ekeland Law. "Human psychology hasn't changed, but the technological tools to manipulate and hack have — to a point where their detrimental effect[s] are much harder to mitigate. It will get worse before it gets better, if ever." The learning experience of attackers figures into that too, said Steve Grobman, McAfee's chief technology officer. "Cyberattacks become more lethal by learning from the successes and failures of previous attacks," he said, while emphasizing the high demand for cyber pros and unfilled jobs. "Election influence campaigns follow this same pattern. For example, adversaries can exploit previously identified weaknesses that have not been remediated, such as the failure to move all election domains to .gov." | | A couple experts called attention to other side-effect threats, like Rep. Jim Langevin (D-R.I.), who was more worried about disinformation and less worried about cyberthreats. "It's also vital to recognize how disinformation raises the threat of electorally motivated violence, including against poll workers and other election administrators, who play such a critical role in the functioning of our free and fair elections," Langevin said. "That, to me, is a much more likely and more concerning threat to our democratic process." Megan Stifel, who said she was less worried about both threats in 2022, was also concerned about some additional issues. "I do worry about the direction of our elections in general as the number of experienced elections administrators is shrinking and the roles are being filled by inexperienced political puppets who give longevity to disproven theories and failed attempts to undermine the 2020 elections and are working to undermine best practices that create opportunities for manipulation," said Stifel, chief strategy officer for the Institute for Security and Technology. | | |  | The network | | - Elizabeth Wharton, vice president for operations at SCYTHE, is more worried about both: "The threat is now coming from inside the house and they now have the script. Domestic actors saw the success of foreign influence campaigns in 2020 and thanks to the extensive 2020 election reporting, they now have the 'how to' playbooks."
- Allan Liska, senior security architect at Recorded Future, is more worried about both: "There was a huge mobilization effort to protect election infrastructure in 2020 as well as active surveillance and takedown of influence campaigns. 2022 is benefiting from some of those built up capabilities and processes. But there is concern that threat actors will, as they always do, change tactics and catch us off guard."
- Shane Huntley, director of Google's Threat Analysis Group, is not more worried about both: "In 2020, Google Tag saw Chinese and Iranian actors targeting email accounts related to the campaigns for then-candidate Joe Biden and then-President Donald Trump. This year, we have not thus seen any direct cyber targeting of campaigns and election officials, and the major cyberthreat actors appear focused elsewhere, so I'm less worried."
- Sam Visner, technical fellow at MITRE, is not more worried about both: "My principal concern is with domestic disinformation amplified through online echo chambers, and possibly strengthened by what some call 'information maneuvers' of foreign adversaries. Better education is the best weapon we can deploy against this threat."
| | |  | The keys | | U.K. politicians call for investigation after report that Russia hacked Truss's phone |  Liz Truss was the United Kingdom's prime minister for six weeks. (Hollie Adams/Bloomberg News) | | | The hack was reportedly discovered over the summer, when Foreign Secretary Liz Truss was vying to be the country's prime minister in a leadership contest, the Mail on Sunday reported. The report about Truss, who went on to become the country's prime minister before resigning this month, hasn't been confirmed by any other major news outlets; however, political rivals have seized on the news, the Associated Press reports. "The newspaper, citing unnamed sources, said Russian spies were suspected of the hack," the AP writes. "It said the hackers gained access to sensitive information, including discussions about the Ukraine war with foreign officials, as well as private conversations between Truss and a political ally, former Treasury chief Kwasi Kwarteng." Layla Moran, a member of parliament who is a spokesperson for the Liberal Democrats party, called for an investigation. Yvette Cooper, a member of Parliament and spokesperson for the main opposition Labour Party, said that the story "raises issues around cybersecurity," telling Sky News that it shows why government officials need to take cybersecurity seriously. The U.K. government has declined to comment on cybersecurity practices but said there are "robust systems in place to protect against cyberthreats," including through regular briefings for ministers. | Biden administration and international allies huddle in Washington to discuss ransomware |  FBI Director Christopher Wray and other top officials will speak at the event, a senior administration official said. (Kevin Dietsch/Getty Images) | | | Representatives of three dozen countries and the European Union will meet with top Biden administration officials for the second meeting of the Counter Ransomware Initiative, which will take place today and Tuesday, according to a senior administration official who spoke with reporters on the condition of anonymity due to ground rules set by the White House. The meeting comes 10 months into the war in Ukraine. "We're seeing the pace and the sophistication of the ransomware attacks increasing faster than our resilience and disruption efforts," the official said, while noting that governments have made significant progress in disrupting the ransomware ecosystem. Top U.S. officials — including FBI Director Christopher A. Wray, national security adviser Jake Sullivan, Deputy Treasury Secretary Wally Adeyemo and Deputy Secretary of State Wendy Sherman — plan to speak at the summit, the official said. | | |  | Securing the ballot | | | |  | Global cyberspace | | | |  | National security watch | | | |  | Daybook | | - Deputy national security adviser Anne Neuberger, National Security Council senior director for cybersecurity and emerging technology Steven Kelly and officials from Canada and France speak at the International Cybersecurity Forum in Montreal on Tuesday and Wednesday.
- CISA Director Jen Easterly and CISA Chief Strategy Officer Valerie Cofield speak at a Center for Strategic and International Studies event Tuesday at 10 a.m.
| | |  | Secure log off | | | Thanks for reading. See you tomorrow. | | |








No comments:
Post a Comment